Securing your PLC Hardware in Siemens TIA Portal
Introduction
This tutorial continues the previous tutorial about Securing your Projects and Programs in Siemens TIA Portal.
In the previous tutorial, we studied the first layer of security within TIA Portal: how to protect your projects and programs. However, these kinds of protections won’t prevent unauthorized access or even cyber attacks against your PLC.
In this tutorial, we will see how to apply a second layer of security to protect your PLC’s access and data integrity using the PLC protection and security options in TIA Portal.
Prerequisites
To follow along with this tutorial, you will need an installation of TIA Portal. We will be using TIA Portal v17, but you can use any other version. No additional hardware or software is required.
PLC protection and security options in TIA Portal
Let’s begin by creating a TIA Portal project and protecting it as shown in the Securing your Projects and Programs in Siemens TIA Portal. Then, open the “Device configuration “in the Project tree.
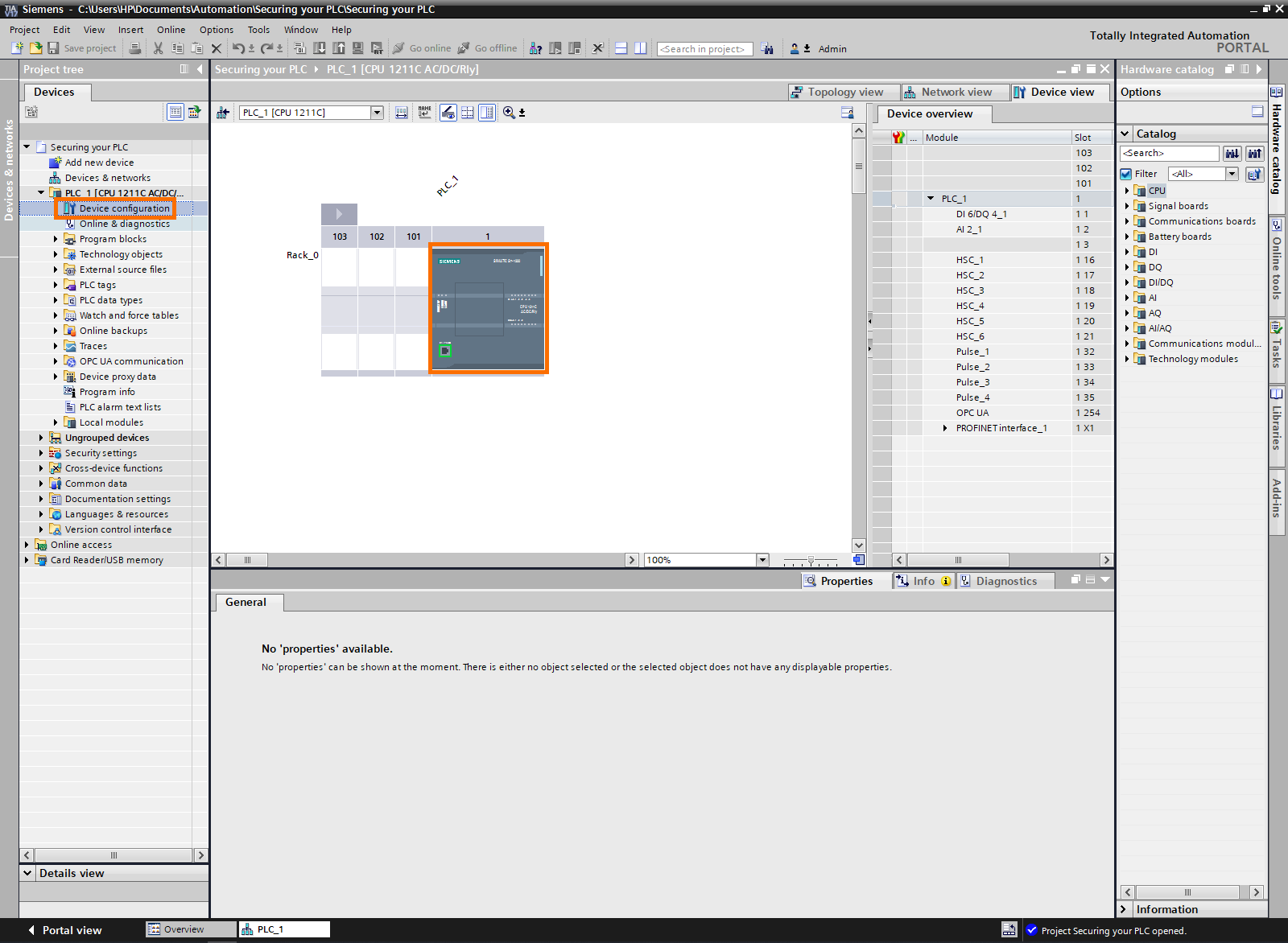
Right-click on the PLC to display its properties on the bottom side of the screen. Scroll down until you find the “Protections & security”
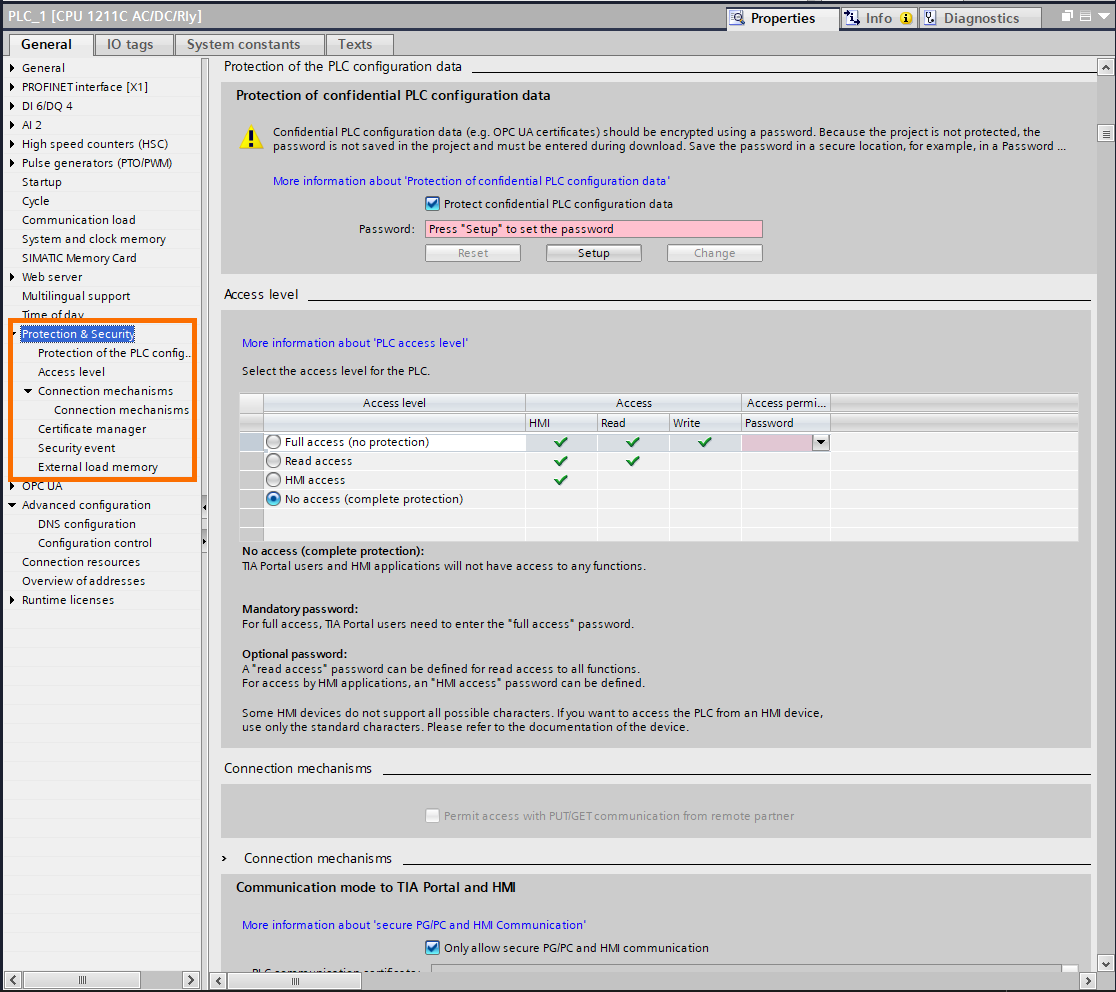
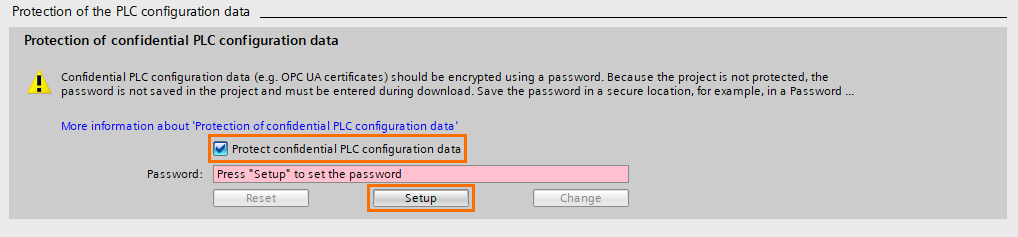
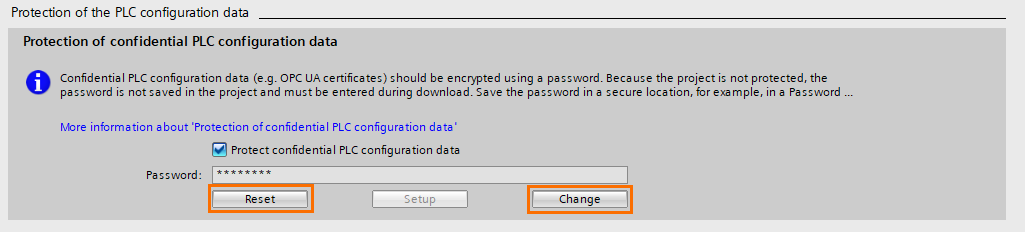
The first security option to activate is the “Protection of confidential PLC configuration data,” This option allows you to apply password-based encryption to all confidential data of the PLC, such as communication protocols’ certificates and PLC configuration.
First, ensure the check-box “Protect confidential PLC configuration data” is checked, then click on “Setup” to define the password.
A “Set password” window will appear, define the password and click on “OK”
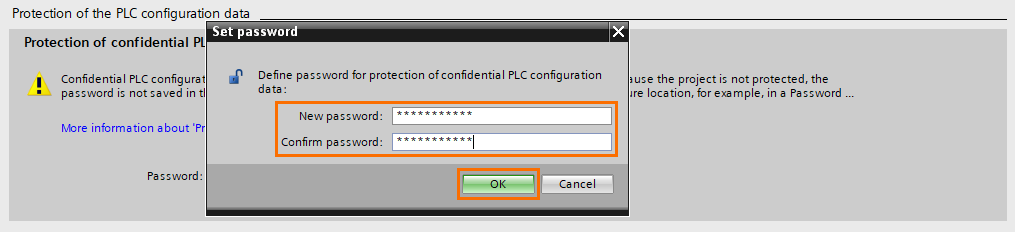
You can change or reset the password with the “Change and Reset” buttons.
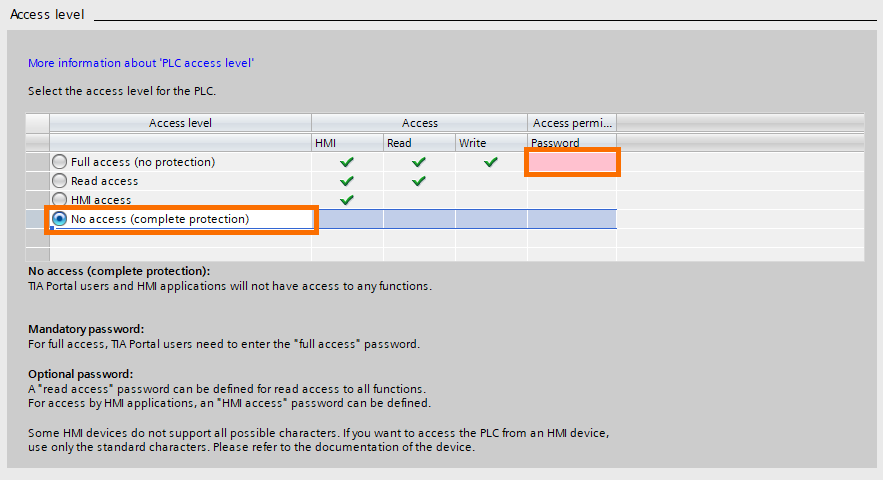
Next is the access level option. You can define an access level for your PLC. The four levels of access are :
- Full access: The PLC can be accessed by any HMI or device in reading and writing. It is the lowest level of security.
- Read access: The PLC can be accessed by any device or HMI in reading only. Data inside the PLC cannot be modified.
- HMI access: The PLC can only be accessed by the HMI.
- No access: No device can access the PLC. It is the highest level of security.
In addition, you can define a password for each level of access. For example, you can set the access level to “No access (complete protection) and specify a password for full access, read access, and HMI access.
The most commonly used access levels are “No access” and “HMI access”.
If your project includes a Siemens HMI, use the “No access” and define an “HMI access” password. This feature is only supported by the Siemens HMIs. Otherwise, use the “HMI access” level.
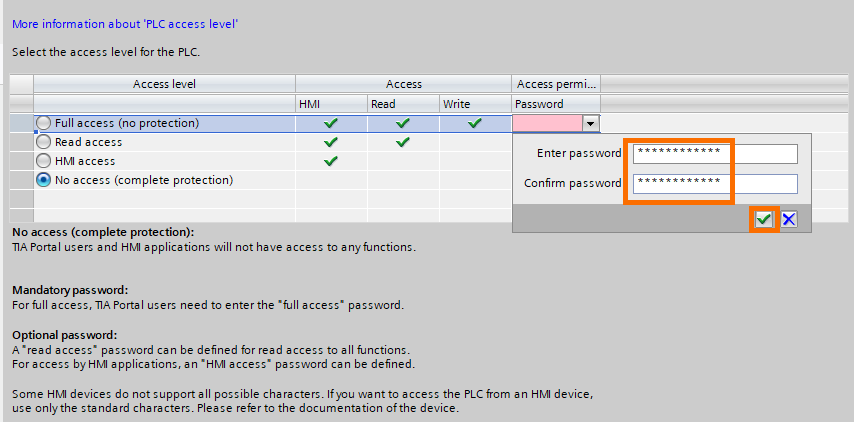
Also, defining a “Full access” password is mandatory. Be sure to keep this password safe. Using a password manager is recommended. To do it, click on “password”
Enter the password and confirm it, then click on the green check mark.
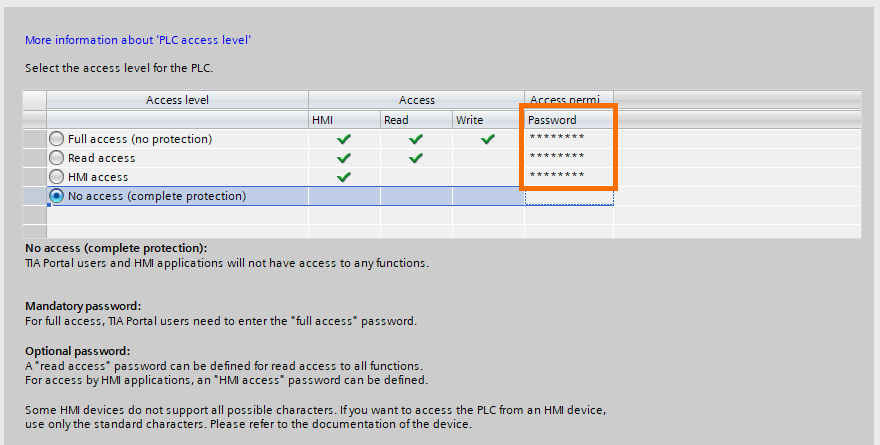
You can repeat this operation to define passwords for the “Read access” and “HMI access”
The third security option is the “Communication mode to TIA Portal and HMI”. This option allows you to use secure and encrypted communications between the PLC, TIA Portal, and HMI. To use it, check the “Only allow secure PG/PC and HMI communication” check box and have the right certificate in the “PLC communication certificate” slot.
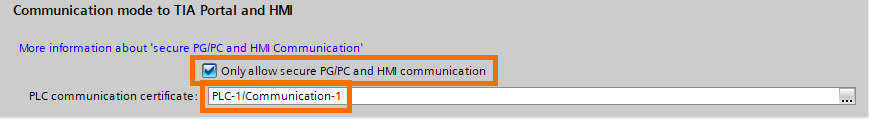
For example, if you want your PLC to communicate only with your PG/PC, you can create a new certificate that will be exclusive to your PG/PC and PLC. You can add a new certificate by clicking on the “...” button followed by “Add new”
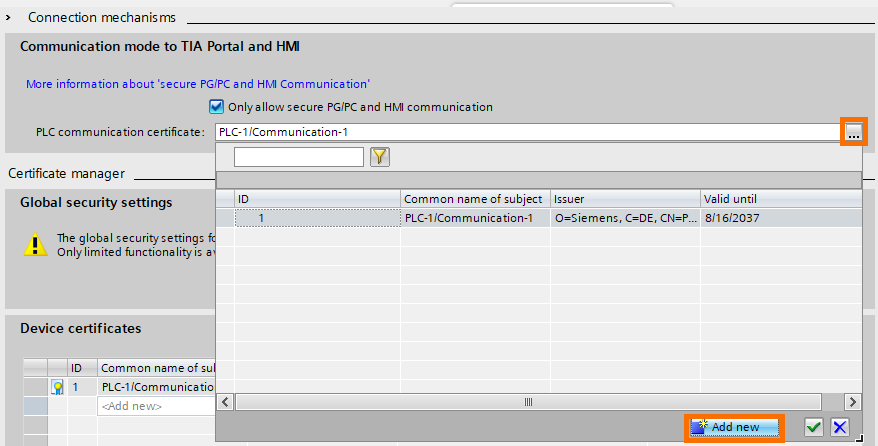
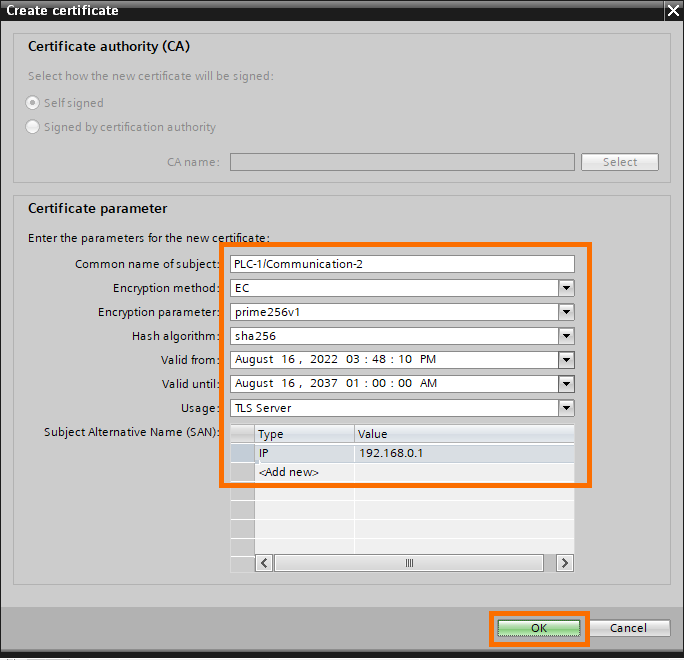
Edit the certificate’s parameters as needed, then confirm by clicking on “OK”
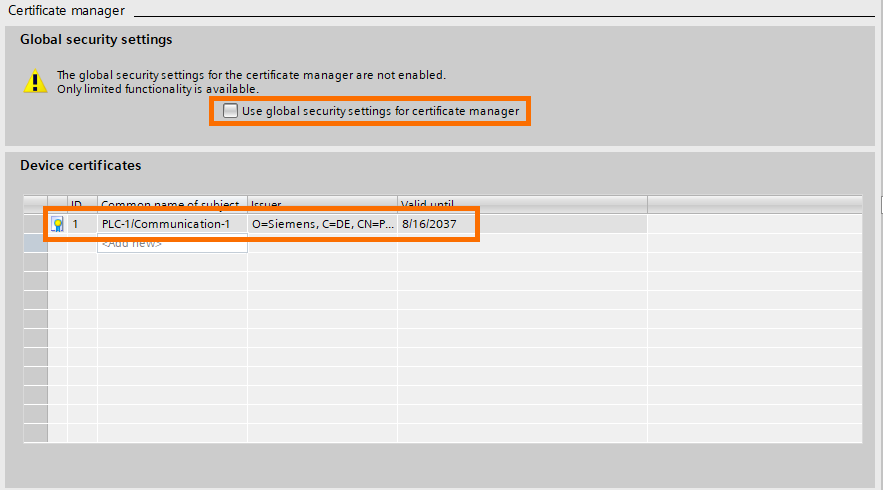
You can manage all certificates in your PLC in the “Device certificates” table. These are the certificates present in your PLC. You can use the “Global security settings” to use the global certificates manager of the project (available in the project’s security features figure 1.12). Use this option to apply your communication certificates to the whole project.
Good practices to keep your PLC secured
There are a lot of features available within the TIA Portal environment that can serve a lot of purposes like the web server for example. However, some of these features can cause security breaches. The prime rule to respect for these kinds of cases is “If you don’t need it, do not activate it”
Here are some examples of features that may represent a risk:
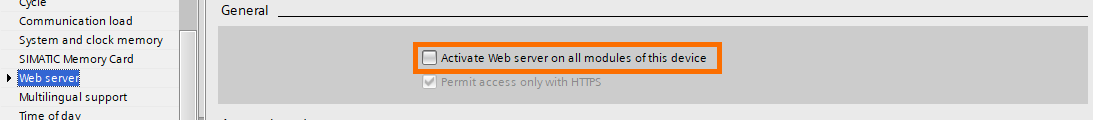
- The web server: activating the web server without the proper security configuration can lead to unauthorized external access.
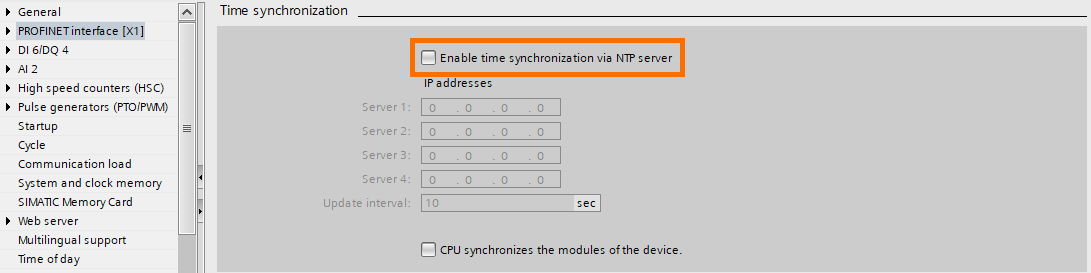
- Time synchronization using an NTP server: Same as for the webserver, Using an NTP server without proper network security can be a breach for cyber attacks.
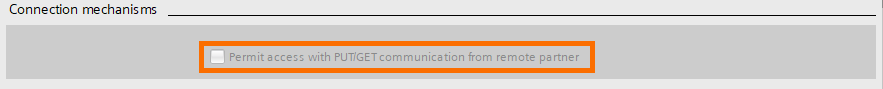
- PUT and GET instructions: These are handy instructions that allow two S7 PLCs to communicate efficiently. However, activating this option can lead to unauthorized access. In the tutorial S7 PLC to PLC Communication, you can learn more about these instructions using GET/PUT Instructions in Siemens TIA Portal.
- IEC V2.2 LLDP mode: The LLDP (Link Layer Discovery Protocol) is a protocol that allows to automatically discover other devices that support it. It can be handy to quickly configure communication between devices that support LLDP. However, it may represent a threat. For example, it can be used as a breach for DOS (Denial Of Service) attacks.
Conclusion
In this tutorial, you learned how to secure your PLC using confidential data encryption, access levels, and other good practices.
PLCs are the most critical part of any industrial system. Securing them is mandatory in order to ensure the reliability and integrity of your process. An attack or a breakdown of the PLC can cause enormous damage. Both economically and materially.
With this second layer of protection, your system is safe from a large specter of cyber threats, but it is still insufficient. There are still a lot of breaches that can be exploited, especially if there are other devices present in your projects such as the HMI or other communication partners which will be treated in the upcoming tutorials.


